
History…
In the early 1990s, phishing emails began tricking people into giving up their login credentials. In 1995, a phishing email tricked employees of a large financial institution into revealing their passwords. This was just the beginning of a trend that has continued to the present day. Since then, phishing emails have become increasingly sophisticated. They now often mimic the branding and design of legitimate websites, making them even more difficult to identify. As a result, phishing emails continue to be a major threat to online security.
Phishing emails trick people into giving up their login credentials. Lax security made phishing emails successful in the past.
Phishing emails compromised over 90% of America Online (AOL) accounts in the early 2000s.
What we have learned…
- Phishing emails are still a major threat today, and the stakes are even higher. In the past, phishing attacks were often limited to stealing personal information, but they can now have a significant impact on financial markets and the global economy. Social media makes it easier for attackers to spread misinformation, which can lead people to click on malicious links or attachments. As a result, phishing attacks are now more likely to be successful, and the potential consequences are even greater.
- People are more likely to click on emails that appear to come from a familiar or authoritative source. Personalized details increase the recipient’s trust, making them more likely to interact with the links or attachments.
- It is important to be careful when opening emails, especially if they contain links or attachments. Verify the sender’s identity and the legitimacy of the message before clicking on anything. If you are unsure, err on the side of caution and do not click on anything.
We provide Cybersecurity solutions at Net56 Technology Services, and we can help stop these attacks before they reach our customers. Learn more at http://net56.com/cybersecurity-solutions/
Activate Your Human Sensors
Over time, security and technical defenses have improved…

- Phishing attacks continue to be a major threat, and they often rely on simple tactics, such as tricking people into clicking on malicious links or providing personal information.
- These emails often create a sense of urgency by threatening to close your account or take legal action if you don’t act immediately.
- They may also pressure you to bypass your security procedures by asking you to click on a link that takes you to a fake website or by asking you to provide your password over the phone.
- If an email or social media post seems too good to be true, it probably is. These emails often offer free prizes, refunds, or other incentives that are simply not possible.
- Legitimate companies and organizations will usually address you by name in their emails. So, if an email starts with a generic greeting like “Dear Customer,” it’s a red flag.
- These emails often ask for sensitive information, such as your credit card number, password, or Social Security number. Legitimate companies will never ask for this information over email.
- The writers of these emails often make mistakes in grammar or spelling, making the emails look unprofessional and suspicious. This is a sign that the email is not from a legitimate source.
- The sender address and reply-to addresses in an email should match. If they don’t, it’s a sign that the email is from a phisher.
- If you receive an email from someone you know, but the tone or wording seems off, it’s possible that the email is from a phisher. Call the sender to verify that they sent the email.
- If you receive an email or social media post that seems suspicious, it’s best to err on the side of caution and not click on any links or provide any personal information.
Be Suspicious

- Be suspicious of everything in your inbox. Be skeptical of every email you receive. Phishing emails are designed to look like they are from legitimate sources, so it is important to be cautious. If an email seems suspicious, do not click on any links or open any attachments.
- Have a process for reporting suspicious emails. Organizations should establish a process for users to report suspicious emails without fear of reprisal.
- Use the feedback from reported emails to educate users. Organizations should provide feedback to users who report suspicious emails, explaining why the email was suspicious and how the user can better identify these emails in the future.
- Share information about scams with users. Organizations should share information about scams with users through security newsletters or other communication channels. This information can help users learn how to identify scams and protect themselves from attack.
- Analyze user reports of suspicious emails. Organizations should analyze user reports of suspicious emails to identify patterns and trends. Organizations can use this information to improve their detection and prevention measures.
- Track individual reporting trends. Organizations should track individual reporting trends over time to identify users who are particularly good at identifying emails. Organizations can provide these users with additional training or resources to help them continue to identify phishing emails.
Additional tips for organizations:
- Use a spam filter. A spam filter can help to reduce the number of phishing emails that users receive.
- Educate users about phishing. Educate users about the dangers of these scams and how to identify phishing emails.
- Use two-factor authentication. Two-factor authentication helps protect users’ accounts from being compromised even if their passwords are stolen.
- Keep software up to date. Software updates often include security patches that can help to protect users from scams and these attacks.
Real Phishing Emails
#1
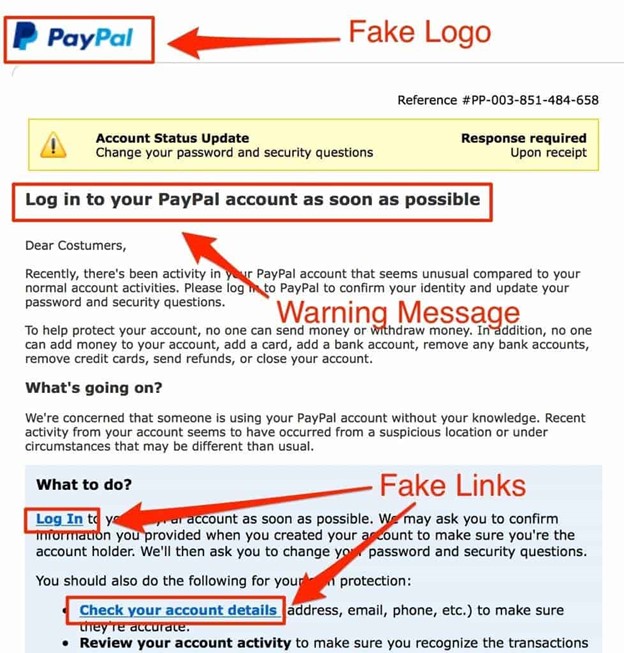
#2
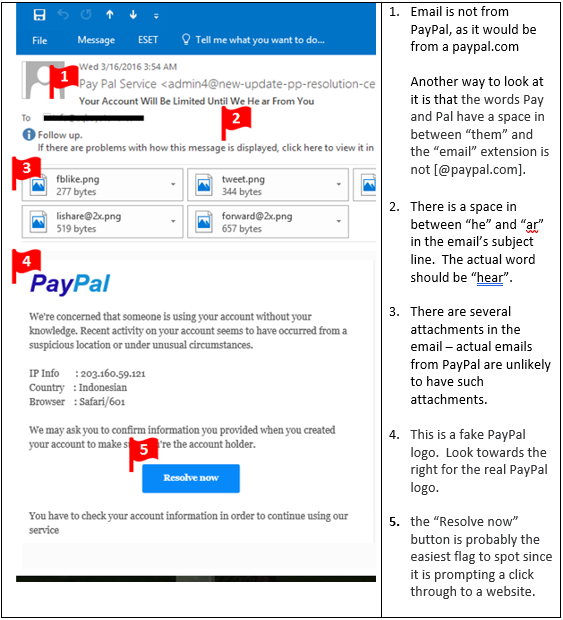
#3
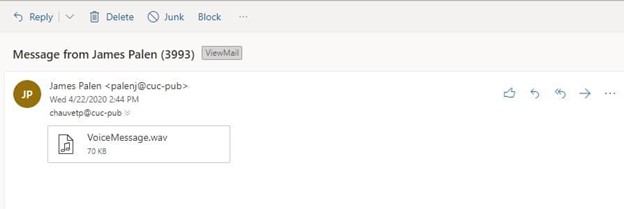
The email contains an attached link that claims to be an audio file called VoiceMessage.wav, but it is actually fake.
The big indication is the email address. The email appears to be from Control Union, however the actual domain name is “cucpublications.controlunion.com”
#4
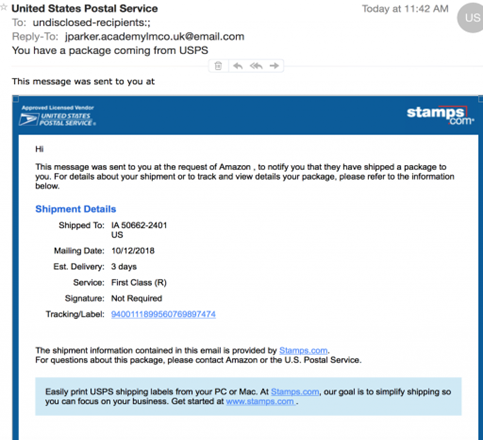
This is one of the oldest phishing emails. What gives it away is the ‘reply to’ entry.
More great resources
IBM has some great information: What is a phishing attack? | IBM
Microsoft: What Is Phishing? | Microsoft Security
KnowBe4 has great tools to educate you: Phishing Security Test (knowbe4.com)




Comments are closed